SLAE ASSIGNMENT 6 | POLYMORPHIC SHELLCODE'S - LINUX X86
Hello Shellcoders,This blog post has been created for completing the requirements of SecurityTube Linux Assembly Expert Certification: http://securitytube-training.com/online-courses/securitytube-linux-assembly-expert/ Student ID: SLAE - 1342
Welcome to Pwsec land. Well if you haven’t read my last blog post in which I completed writing my SLAE Assignment 5 blog post on “METASPLOIT SHELLCODE'S ANALYSIS - LINUX X86”, then you can check it [Here]. Today in this post we will be creating three Polymorphic Linux x86 Shellcodes which we will take from the shell-storm website. So the requirement for the sixth SLAE exam assignment is:
- Take up 3 shellcode from shell-storm and create a polymorphic version of them to beat the pattern matching.
- The polymorphic versions can not be larger than 50% of the existing shellcode.
- Bonus point for making it shorter in length than original
I have chosen these three shellcodes.
- http://shell-storm.org/shellcode/files/shellcode-842.php
- http://shell-storm.org/shellcode/files/shellcode-542.php
- http://shell-storm.org/shellcode/files/shellcode-758.php
So I have selected these three shellcodes for the completion of this assignment.
Let’s first understand what a polymorphism is by wikipedia :- In computer terminology, polymorphic code is a code that uses a polymorphic engine to mutate while keeping the original algorithm intact. That is, the code changes itself each time it runs, but the function of the code (its semantics) will not change at all. For example, 1+3 and 6-2 both achieve the same result while using different values and operations. This technique is sometimes used by computer viruses, shellcodes and computer worms to hide their presence.
Also I have written comments with my polymorphic version of the shellcode.
Also I have written comments with my polymorphic version of the shellcode.
Polymorphic shellcode 1
So this is a shellcode which will try to read the first 4096 bytes from /etc/passwd file. The author of this shellcode is geyslan. You can find the shellcode [here].Let’s run it,
So the original shellcode length is 57 Bytes currently, and as you can see it printed out the contents of /etc/passwd.
Here is the polymorphic version of this shellcode.
Let's run it,
Now the shellcode length is: 59 Bytes
[Note:Please refer to this video if you also don’t know how to calculate the percentage increase.]
Size Increased by: 3.5%
Polymorphic shellcode 2
So this is a shellcode which will try to create a directory with the name “Hacked”. The author of this shellcode is zillion. You can find the shellcode [here]Let’s run it,
So the original shellcode length is 36 Bytes currently, and as you can see it just created a new directory with the name “hacked”.
Here is the polymorphic version of this shellcode.
Let’s run it,
Now the shellcode length is: 35 Bytes
Size Decreased by: 2.7%
Polymorphic shellcode 3
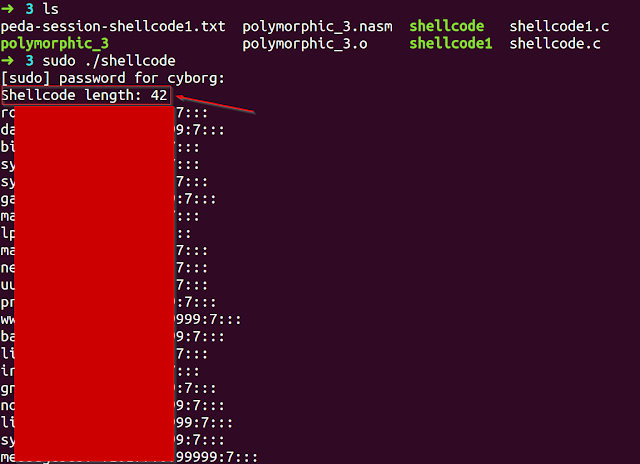
So this is a shellcode which will try to read try to read the file /etc/shadow using /bin/cat command. It will be using execve function to execute this command. The author of this shellcode is antrhacks. You can find the shellcode [here]Let’s run it,
So the original shellcode length is 42 Bytes currently, and as you can see it printed out the contents of /etc/shadow file.
Here is the polymorphic version of this shellcode.
Let’s run it,
Now the shellcode length is: 51 Bytes
Size Increased by: 21.4%
Pretty easy, huh? If you still have any doubt, then please feel free to ping me on twitter [@Pwsecspirit]
Thanks,












Post a Comment:
Please tell us if we have done anything wrong :) and please share our website if you like.